
Advanced Reconnaissance and Exploitation Techniques
Advanced reconnaissance and exploitation techniques are pivotal in modern cybersecurity efforts.
Duration
30h
Lessons
18
Students
1.2k
Rating
4.9
0% Completed
350 XP
Module 1
Professional Bug Hunter
Advanced
Sign in to Access
Please sign in to access this content.
First time? You'll receive a verification code via email to sign in securely.
Web Reconnaissance
45m
Introduction
Web Reconnaissance is a fundamental part of a security assessment. It involves systematically collecting and analyzing data about a target website or application. Think of it as the initial phase of a penetration test, forming the core of the Information Gathering stage.
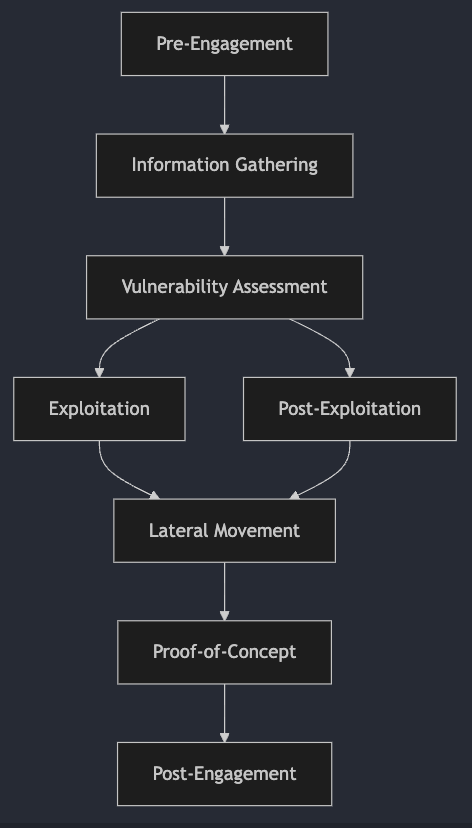
The primary objectives of web reconnaissance include:
- Identifying Assets: Uncovering publicly available components such as web pages, subdomains, IP addresses, and technology stacks.
- Discovering Exposed Data: Finding hidden or sensitive information like backup files, configuration details, or internal documentation.
- Analyzing Attack Surface: Assessing web technologies, configurations, and entry points for potential exploitation.
- Gathering Intelligence: Collecting data useful for further attacks, including key personnel, email addresses, and organizational patterns.
Both ethical hackers and malicious actors use reconnaissance techniques—one to improve security and the other to identify weaknesses to exploit.
Types of Reconnaissance
Web reconnaissance is divided into two main approaches: Active and Passive reconnaissance. Each method has unique advantages and considerations.
Active Reconnaissance
Active reconnaissance involves direct interaction with the target system to retrieve information. It is more effective in gathering details but has a higher risk of detection.
| Technique | Description | Example | Tools | Risk of Detection |
|---|---|---|---|---|
| Port Scanning | Identifying open ports and running services. | Scanning a target web server for open ports like 80 (HTTP) and 443 (HTTPS). | Nmap, Masscan | High |
| Vulnerability Scanning | Searching for security flaws and misconfigurations. | Running OpenVAS to find SQL injection vulnerabilities. | Nessus, Nikto | High |
| Network Mapping | Discovering network structure and connected devices. | Using traceroute to analyze data packet paths. | Traceroute, Nmap | Medium-High |
| Banner Grabbing | Retrieving service information from headers. | Checking an HTTP response header for software versions. | Netcat, Curl | Low |
| OS Fingerprinting | Identifying the target's operating system. | Running Nmap's -O flag to detect OS details. | Nmap, Xprobe2 | Low |
| Service Enumeration | Determining service versions. | Using nmap -sV to identify web server versions. | Nmap | Low |
| Web Spidering | Crawling a site for content discovery. | Running Burp Suite Spider to map a web application. | Burp Suite, ZAP Spider | Low-Medium |
Active reconnaissance provides detailed insights into the target but has a high likelihood of triggering security defenses like Intrusion Detection Systems (IDS) and firewalls.
Passive Reconnaissance
Passive reconnaissance collects information without directly interacting with the target. Instead, it relies on public sources and open databases.
| Technique | Description | Example | Tools | Risk of Detection |
|---|---|---|---|---|
| Search Engine Queries | Using search engines to find information. | Googling site:target.com filetype:pdf to locate documents. | Google, Bing, Shodan | Very Low |
| WHOIS Lookups | Checking domain registration details. | Running a WHOIS query on a target domain. | WHOIS lookup tools | Very Low |
| DNS Analysis | Gathering DNS records and subdomains. | Using dig to enumerate DNS records. | Dig, DNSenum, Fierce | Very Low |
| Web Archive Analysis | Examining old website versions. | Checking Wayback Machine for past data leaks. | Wayback Machine | Very Low |
| Social Media Analysis | Gathering intelligence from social networks. | Searching LinkedIn for employee profiles. | LinkedIn, Twitter, OSINT tools | Very Low |
| Code Repositories | Searching for sensitive code leaks. | Checking GitHub for exposed credentials. | GitHub, GitLab | Very Low |
Passive reconnaissance is more stealthy but may not provide as much actionable information as active methods.
Moving Forward
This module explores essential reconnaissance tools and techniques, starting with WHOIS lookups. Mastering these methods enables security professionals to collect critical information while minimizing exposure. As we progress, we will explore advanced reconnaissance strategies that complement these foundational concepts.
Questions
- What are the key differences between active and passive reconnaissance, and how do they impact detection risk?
- Can you think of a scenario where passive reconnaissance might provide more useful information than active reconnaissance?